

CSR Privacy Solutions
ATI Secure Docs is proud to introduce a new service to our customers: CSR Privacy Solutions. CSR delivers easy and intuitive data privacy tools that you can integrate into your existing business to improve both your internal information security and your defense against a data breach.
Choose the CSR solution that best meets the needs of your company and improve your privacy protection today!
Protect the Personally Identifiable Information (PII) of Your Employees and Customers
PII is any information that can identify an individual and possibly lead to identity theft or fraud. All businesses have PII, it comes from customers, employees, and vendors and is usually found in every department. It can be as obvious as a social security number or just an email address or phone number.
Protect Yourself and Your Business
Many laws cover the retention and/or destruction of PII, breach, and consumer notification protocol. Your responsibility for data protection encompasses all paper records and electronic files containing PII.
ATI Secure Docs Readiness Pro Edition, powered by CSR, will help your business reduce the risk of a data breach, and in the event of an actual or suspected breach, CSR takes the headache and hassle out of the legal requirements to report the loss or breach of PII to an ever-increasing number of authorities, as well as mandated notification to your customers.
How CSR Benefits Your Business
- Save time and money
- Provide you and your customers with peace of mind
- Makes privacy laws clear and easy to act on
- Mitigates risks from incorrect breach reporting
- Effortlessly fulfill breach reporting requirements
- Simplify your privacy and incident response plans
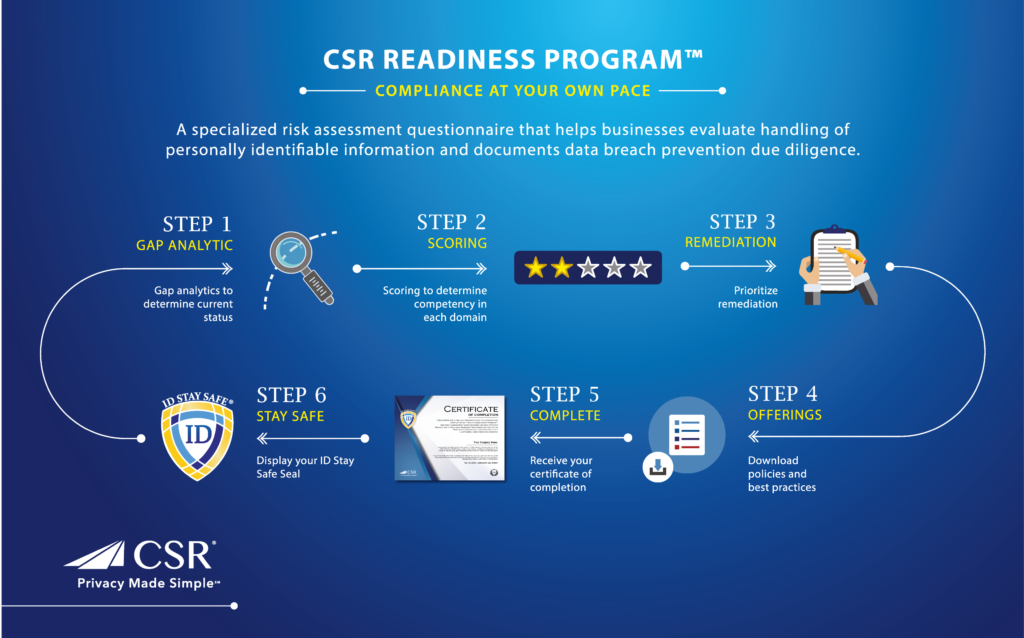
What is CSR Readiness®?
The core element of the CSR Readiness® program is a specialized risk assessment questionnaire, which you can use to conduct a thorough evaluation of your existing information and data breach protection standards. Once you’ve established the areas that require improvement, the CSR Readiness® program will automatically generate remediation instructions, policies, and suggested best practices for you to implement.
This includes:
- Compliance
- Security
- Audits
- Incident Response Planning
Once you’ve made the recommended adjustments, you’ll receive a CSR Readiness Certificate of Completion, which publicly attests to the fact that your business carefully and correctly handles personal and confidential information.
How CSR Readiness Works: Three Simple Steps
- A self-assessment data privacy questionnaire
- Generation of remediation instructions, policies, and best practices regarding compliance, security, incidence response planning and audit
- 24/7 access to allow ongoing input and regular monitoring
Breach Reporting Service (BRS)
The Breach Reporting Service is the reactive counterpart to CSR Readiness. In the event of a data breach, this solution fulfills your legal requirement to report the breach and notify your customers. This patented, award-winning service is provided by Certified Information Privacy Professionals and will help protect your reputation and mitigate fines.
Four Easy Steps
- Collect all necessary information
- Call the toll-free number: 888-301-6449
- The CSR Privacy Professional will evaluate the incident using the powerful and patented CSR systems
- CSR completes all necessary reporting and, if needed, works with the user to complete consumer notification


ATI Secure Docs Readiness® Pro Edition
The Readiness® Pro Edition will help your business reduce the risk of a data breach, and in the event of an actual or suspected breach, CSR takes the headache and hassle out of the legal requirements to report the loss or breach of PII to an ever-increasing number of authorities, as well as mandated notification to your customers.
Readiness® Pro comes complete with the original Readiness® program as well as the award-winning Breach Reporting System.
Watch CSR’s Breach Reporting Service and Readiness videos to learn why reporting and notification are mandatory, how the service works, and who the experts are behind it.
Discover the #1 data privacy solution for small to medium sized businesses.
The Texas Privacy Protection Act
Texas Governor Greg Abbot signed into law the Texas Privacy Protection Act (“TPPA”) which amends Texas’ existing breach notification law, the Texas Identity Theft Enforcement and Protection Act (“TITEPA”) and creates the Texas Privacy Protection Advisory Council (the “Council”). The TPPA is in effect as of January 1, 2020.
Per the TPPA, “persons conducting business in Texas and owns or licenses computerized data that includes sensitive personal information” of Texas residents, who experience a breach of security, must provide consumer notification to all affected state residents without unreasonable delay and no later than 60 days from the date of discovery of the breach.
Reporting must also be provided to the attorney general when the breach involves at least 250 Texas residents, and must be made no later than 60 days from the date of discovery of the breach. The contents of the breach reporting to the attorney general must include:
- A detailed description of the nature and circumstances of the breach or the use of sensitive
personal information acquired as a result of the breach; - The number of residents of this state affected by the breach at the time of notification;
- The measures taken by the person regarding the breach;
- Any measures the person intends to take regarding the breach after the notification under this
subsection; and - Information regarding whether law enforcement is engaged in investigating the breach.
Businesses handling the personal information of Texas residents must implement an incident response plan for investigating and responding to security breach incidents, including employee and vendor breach training and awareness.
CSR Privacy Solutions, Inc. can ease the tension small to medium size businesses (SMB) may feel with implementing and keeping up to date with necessary policies and procedures. We are privacy made simple with a focus on risk awareness, avoidance, and evaluation.
Got Questions? Check Out Our CSR FAQ Page!
States With Mandatory PII Security Programs
8-38-3 Alabama Data Breach Notification Act of 2018: Covered entities and their third-
party agents must implement and maintain reasonable security measures to protect sensitive personally identifying information (PII) against a breach of security. Examples of
some measures include adoption of appropriate information safeguards to address
identified risks of a breach of security and assess the effectiveness of such safeguards; and
evaluation and adjustment of security measures relative to changes in circumstances
affecting the security of sensitive PII.
45.48.500 Personal Information Protection Act – Disposal of Records: When disposing of
records that contain personal information, a business and a governmental agency shall
take all reasonable measures necessary to protect against unauthorized access to or use of
the records such as implementing and monitoring compliance with policies and
procedures that require the burning, pulverizing, or shredding of paper documents and the
destruction or erasure of electronic media and other non-paper media containing personal
information so that the personal information cannot practicably be read or reconstructed.
4‐110‐104 Protection of Personal Information: A person or business that acquires, owns,
or licenses personal information about an Arkansas resident shall implement and maintain
reasonable security procedures and practices appropriate to the nature of the information
to protect the personal information from unauthorized access, destruction, use,
modification, or disclosure, including taking all reasonable steps to destroy or arrange for
the destruction of P.I. no longer needed by shredding, erasing, or otherwise modifying it so
that it is made unreadable or undecipherable.
36-3806. Required policies: A health information organization must implement and
enforce policies governing the privacy and security of individually identifiable health
information, including, but not limited to,
- addressing security safeguards to protect individually identifiable health
information, as required by the health insurance portability and accountability act
security rule, 45 Code of Federal Regulations part 164, subpart C. - Appointing responsible person(s) to maintain privacy and security procedures; and
- Biannual training of employees and agents.
15-1046. Student data privacy: Operator must Implement and maintain reasonable
security procedures and practices that are appropriate to the nature of the covered
information and that are designed to protect that covered information from unauthorized
access, destruction, use, modification or disclosure.
1798.81.5.: A business that owns, licenses, or maintains personal information about a
California resident shall implement and maintain reasonable security procedures and
practices appropriate to the nature of the information, to protect the personal information
from unauthorized access, destruction, use, modification, or disclosure and require the
same of nonaffiliated third parties by contract.
6-1-713.5. Protection of personal identifying information a covered entity must
implement and maintain “reasonable security procedures and practices that are
appropriate to the nature of the [PII] and the nature and size of the business and its
operations, and require the same of their contracted vendors, who maintains, stores or
processes the P.I. that the covered entity discloses to them.” Colo. Rev. Stat. § 6-1-713.5(1).
A covered entity must develop and maintain policies and procedures to govern
the destruction and disposal of both paper and electronic documents containing PII, by
shredding, erasing, or otherwise modifying it rendering it unreadable or
indecipherable. Colo. Rev. Stat. § 6-1-713(1).
38a-999b. Comprehensive information security program to safeguard personal
information. A health related company shall implement and maintain a written
comprehensive information security program, containing administrative, technical and
physical safeguards for the security, confidentiality or integrity of any electronic, paper or
other records that contain personal information, and that are appropriate to the
company’s size, resources available and amount of data collected from insureds and
enrollees that is compiled or maintained by such company. Contracted vendors who have
access to covered entity’s P.I. are required to implement the same standards. Each year
said company must send a certification to Insurance Department that it is in compliance
with maintaining a comprehensive information security program.
12B-100 Protection of personal information. Any person who conducts business in this
State and owns, licenses, or maintains computerized personal information shall implement
and maintain reasonable procedures and practices to prevent the unauthorized
acquisition, use, modification, disclosure, or destruction of personal information collected
or maintained in the regular course of business.
38–831.02. Operator obligations. An operator providing services to an educational
institution, and any of its vendors in receipt of disclosed student personal information,
must implement and maintain reasonable security policies and procedures appropriate to
the nature of the personally identifiable student information, and designed to protect that
information from unauthorized access, destruction, use, modification, or disclosure.
501-171(2); (8). REQUIREMENTS FOR DATA SECURITY: Each covered entity and their
third-party agent must take reasonable measures to protect and secure data in electronic
form containing personal information as well as to dispose, or arrange for the disposal, of
customer records containing personal information within its custody or control when the
records are no longer to be retained by shredding, erasing, or otherwise modifying the
records to make them unreadable or undecipherable through any means.
10-15-2. Disposal of business records containing personal information: A business
must discard records containing P.I. by shredding, erasing, or otherwise modifying the
records to make them unreadable and take actions ensuring no unauthorized person will
have access between its disposal and destruction of a customer’s record.
§487R-2 Destruction of personal information records: Any business or government
agency shall take reasonable measures to protect against unauthorized access to or use of
the information in connection with or after its disposal by implementing and monitoring
written policies and procedures that require the burning, pulverizing, recycling, or
shredding of papers, and destruction or erasure of electronic media and other non-paper
media containing personal information so that the information cannot practicably be read
or reconstructed, and/or contracting with a an actual disposal business who has adequate
protections during or after the collection, transportation and disposal of the personal
information of residents.
815 ILCS 530/45: A data collector that owns or licenses, or maintains or stores but does
not own or license, records that contain personal information concerning an Illinois resident, and a contracted vendor who receives P.I. from data collector, shall implement
and maintain reasonable security measures to protect those records from unauthorized
access, acquisition, destruction, use, modification, or disclosure.
815 ILCS 530/40: A person must dispose of the materials containing personal information
in a manner that renders the personal information unreadable, unusable, and
undecipherable. If in the form of paper, by either redacting, burning, pulverizing, or
shredding, and destroying or erasing any non-paper/electronic media so that it cannot be
read or reconstructed. Vendor/Third-Party contracted to dispose of PI – must implement
and monitor compliance with policies/procedures that prohibit unauthorized access to or
acquisition of or use of personal information during the collection, transportation, and
disposal of materials containing personal information.
740 ILCS 14/15: A private entity in possession of authorized biometric identifiers or
biometric information must develop a publicly available written policy, establishing a
retention schedule and guidelines for permanently destroying it when the initial purpose
for collecting or obtaining it has been satisfied or within 3 years an individual’s last
interaction with the private entity, as well as taking measures that are adequate or more
restrictive than the standard of storing, protecting or transmitting other types of
confidential and sensitive information.
IC 24‐4.9‐3‐3.5: A data base owner shall implement and maintain reasonable procedures,
including taking any appropriate corrective action, to protect and safeguard from unlawful
use or disclosure any personal information of Indiana residents collected or maintained by
the data base owner.
A data base owner with records or documents in any form that are unencrypted and
unredacted personal information of Indiana residents must dispose of them by shredding,
incinerating, mutilating, erasing, or otherwise rendering the personal information illegible
or unusable.
50-6,139b. Requirements for holders of personal information: A holder of personal
information, in the course of ordinary business, must implement and maintain reasonable
procedures and practices appropriate to the nature of the information and protect the
personal information from unauthorized access, use, modification or disclosure. Such
holder should also take reasonable steps to destroy or arrange for the destruction of any
records within their custody or control, containing P.I. when holder no longer intends to
maintain or possess those records, by shredding, erasing or otherwise modifying them to
make them unreadable or undecipherable through any means.
365.725 Destruction of customer’s records containing personally identifiable
information: Business must take reasonable steps to destroy of arrange for the
destruction of any customer’s records containing personally identifiable information that
are no longer required to retain, by shredding, erasing, or otherwise modifying those
records to make them unreadable or indecipherable through any means.
RS 51:3074. Protection of personal information: Any person or agency that conducts
business in the state or that owns or licenses computerized data that includes personal
information, shall implement and maintain reasonable security procedures and practices
appropriate to the nature of the information to protect the personal information from
unauthorized access, destruction, use, modification, or disclosure, and must also destroy
or arrange for the destruction of those records no longer needed by shredding, erasing, or
otherwise modifying the personal information in the records to make it unreadable or
undecipherable through any means.
§9301. Privacy of broadband Internet access service customer personal information
Security of customer personal information. A provider shall take reasonable measures to
protect customer personal information from unauthorized use, disclosure or access, by
implementing reasonable security measures depending on the nature of their activities,
sensitivity of data collected, and size of provider.
14‐3503 Reasonable security procedures and practices: Business to protect personal
information from unauthorized access, use, modification, or disclosure, a business that
owns or licenses personal information of an individual residing in the State shall
implement and maintain reasonable security procedures and practices that are
appropriate to the nature of the personal information owned or licensed and the nature
and size of the business and its operations and when business is destroying a customer’s,
an employee’s, or a former employee’s records that contain personal information.
Business must require, by written contract with vendor (nonaffiliated) who performs
services for the business and discloses P.I. of a resident, to implement and maintain the
same reasonable security practices and procedures.
201 CMR 17.01: This regulation establishes minimum standards to be met in connection
with the safeguarding of personal information contained in both paper and electronic
records. The objectives of this regulation are to insure the security and confidentiality of
customer information in a manner fully consistent with industry standards; protect against
anticipated threats or hazards to the security or integrity of such information; and protect
against unauthorized access to or use of such information that may result in substantial
harm or inconvenience to any consumer.
17.03: Every person that owns or licenses personal information about a resident of the
Commonwealth shall develop, implement, and maintain a comprehensive information
security program that is written in one or more readily accessible parts and contains
administrative, technical, and physical safeguards that are appropriate to the company
size, available resources, amount of stored data and security needs. Such
implementations consist of designation of employee(s) to maintain program, risk
assessments, employee training and disciplinary measures, service provider/vendor
oversight, annual assessment, mandatory post‐incident review after breach, specific
secure user authentication protocols, encryption, system monitoring, etc.
325M.05 SECURITY OF INFORMATION: Internet service providers must take reasonable
steps to maintain the security and privacy of a consumer’s personally identifiable
information.
NRS 603A.210: A business or its contracted vendor, who maintains records which contain
personal information of a resident of this State, shall implement and maintain reasonable security measures to protect those records from unauthorized access, acquisition,
destruction, use, modification or disclosure. Reasonable measures for the destruction of
records includes any way that renders the documentation unreadable or undecipherable
to include such actions as shredding or erasure.
420-P:4 Insurance Licensees have until 1/1/2021 to develop, implement and maintain a
comprehensive information security program, based on the licensee’s risk assessment and
commensurate with their size and complexity, and the nature and scope of the licensee’s
activities, including its use and management of third-party service providers (effective
1/1/2022), and the sensitivity of the nonpublic information used by the licensee or in the
licensee’s possession, custody, or control, and that contains administrative, technical, and
physical safeguards for the protection of nonpublic information and the licensee’s
information system.
HB 15, Chapter 36: A persona that owns or licenses personally identifiable information
(PII) of a New Mexico resident must implement and maintain reasonable security
procedures and practices appropriate to the nature of the PII to protect from unauthorized
access, use, modification or disclosure.
646A.622: A covered entity and a vendor shall develop, implement and maintain
reasonable safeguards to protect the security, confidentiality and integrity of the personal
information, including administrative, technical and physical safeguards, such as data
destruction, third party contracts, risk assessment, designated security/privacy officer, and
employee training, and that protect the personal information when the covered entity and
a vendor disposes of the personal information, and can use these measures to affirmative
defend against a breach violation of safeguards.
11‐49.3‐2: A municipal agency, state agency, or person who or that stores, collects,
processes, maintains, acquires, uses, owns, or licenses personal information about a
Rhode Island resident shall implement and maintain a risk‐based information security
program that contains reasonable security procedures and practices appropriate to the
size and scope of the organization; the nature of the information; and the purpose for
which the information was collected in order to protect the personal information from
unauthorized access, use, modification, destruction, or disclosure and to preserve the
confidentiality, integrity, and availability of such information. Nonaffiliated third parties
who receive such information shall be required by written contract to also implement and
maintain reasonable security procedures and practices.
6-52-2: Safe destruction of documents. – A business shall take reasonable steps to destroy
or arrange for the destruction of a customer’s personal information within its custody and
control that is no longer to be retained by the business by shredding, erasing, or otherwise
destroying and/or modifying the personal information in those records to make it
unreadable or indecipherable ensuring its security and confidentiality from foreseeable
threats or unauthorized access or use.
37-20-190. Requirements for disposition of business records – Business must take steps
to ensure disposal of data containing personal information by shredding, erasing or
otherwise modifying it to make it unreadable or undecipherable, and/or may contract with
a person engaged in the business of disposing of records containing personal information
to do so.
521.052: BUSINESS DUTY TO PROTECT SENSITIVE PERSONAL INFORMATION. A business
shall implement and maintain reasonable procedures, including taking any appropriate
corrective action, to protect from unlawful use or disclosure any sensitive personal
information collected or maintained by the business in the regular course of business,
including destruction or arranging for destruction of records, not to be retained by the
business, by shredding, erasing or otherwise modifying making the information
unreadable or indecipherable.
39-14-150 Any private entity or business who destroys a record containing a customer’s
personal information must have minimum standard policies and practices in place to
ensure destruction of such records by shredding, erasing, burning or otherwise modifying
it making it unreadable or takes action to ensure there is no unauthorized access to
personal information contained in such record(s) from the time between its disposal and
destruction.
49-1-703 (3)– Board of Education shall develop a detailed data security plan containing
guidelines for authorizing access to the teacher data system, the student data system,
privacy compliance standards and security audits, breach planning including notification
procedures and data retention and disposition policies. Any private vendors shall have
contracts in place to include privacy and security provisions and penalties for
noncompliance.
49-1-708 (c)(1) – A k-12 internet website / online service operator must implement and
maintain reasonable security procedures and practices appropriate to the nature of the
covered information, designed to protect that covered information from unauthorized
access, destruction, use, modification, or disclosure and delete student’s covered
information within a reasonable time.
13‐44‐201: Any person who conducts business in the state and maintains personal
information shall implement and maintain reasonable procedures to: prevent unlawful use
or disclosure of personal information collected or maintained in the regular course of
business.
2445. Safe destruction of documents containing personal information – Business or
entity who is a data destruction business disposes of personal information of residents of
Vermont must take all reasonable measures to dispose of records containing personal
information by implementing and monitoring compliance with policies and procedures
that protect against unauthorized access to or use of personal information during or after
the collection and transportation and disposing of such information.
2447. Data broker duty to protect information; standards; technical requirements –
Data broker shall develop, implement, and maintain a written, accessible and extensive
comprehensive information security program containing administrative, technical, and
physical safeguards, including, among many things, designation of employee to maintain
the program, conduct internal and external risk assessments, employee training, employee
related security policies and disciplinary measures, access restrictions, third party service
provider due diligence and oversight, including but not limited to, ensuring contracts are in
place to ensure provisions including security policies and practices are being implemented
on their end for protecting personal information received.
22.1-289.01. School service providers; school-affiliated entities; student personal
information – In operating a school service pursuant to a contract with a local school division, each school service provider shall maintain a comprehensive information security
program that is reasonably designed to protect the security, privacy, confidentiality, and
integrity of student personal information and makes use of appropriate administrative,
technological, and physical safeguards and require any successor entity or third party with
whom it contracts to abide by its policy for the privacy of student personal information
and comprehensive information security program before accessing student personal
information.
19.215.005 – Entities and individuals have a continuing obligation to ensure the security
and confidentiality of personal information during the process of disposing of that
information by having disposal policies and methods that protect individuals from identity
theft through unauthorized use and access. An entity must take all reasonable steps to
destroy, or arrange for the destruction of, personal financial and health information and
personal identification numbers issued by government entities in an individual’s records
within its custody or control when the entity is disposing of records that it will no longer
retain.
Board of Education shall develop a detailed data security plan containing guidelines for
authorizing access to the student data system, privacy compliance standards and security
audits, breach planning including notification procedures, data retention and disposition
policies and data security policies including electronic, physical, and administrative
safeguards, such as data encryption and training of employees. Any private vendors shall
have contracts in place to include privacy and security provisions and penalties for
noncompliance.
134.97 Disposal of records containing personal information – A financial institution,
medical business or tax preparation business, may not dispose of a record containing
personal information unless the financial institution, medical business, tax preparation
business or other person under contract with the financial institution, medical business or
tax preparation takes actions to ensure that no unauthorized person obtains access from
the time of disposal and destruction of the record by taking steps to shred, erase or
otherwise modify it making it unreadable.
21-2-202. Duties of the state superintendent – The state superintendent and the
department of enterprise technology services shall develop a data security plan that
includes guidelines for accessing student data; privacy compliance standards and security
audits; breach planning including notification procedures; and data retention and
disposition policies; data security policies including electronic, physical and administrative
safeguards such as data encryption and employee training; and prohibition of the sale of
student data to private entities.


